Magento is one of the leading eCommerce platforms. More than 30% of businesses in the industry have opted for this CMS, according to BuiltWith.
Working with Magento eCommerce sites (now Adobe Commerce) for more than a decade, we come across a multitude of well-structured, high-performing, SEO-optimized, and well-designed Magento stores that are worth being highlighted.
Our list of the top 15 world’s biggest Magento sites is based on their structure, load speed, navigation, UX and mobile-friendliness. These brands are big and famous. You are welcome to share your feedback on the selection we offer and recommend your favorite companies using Magento in the comments field below the article.
Table of Contents
Top 15 Best Magento Websites That Use Magento
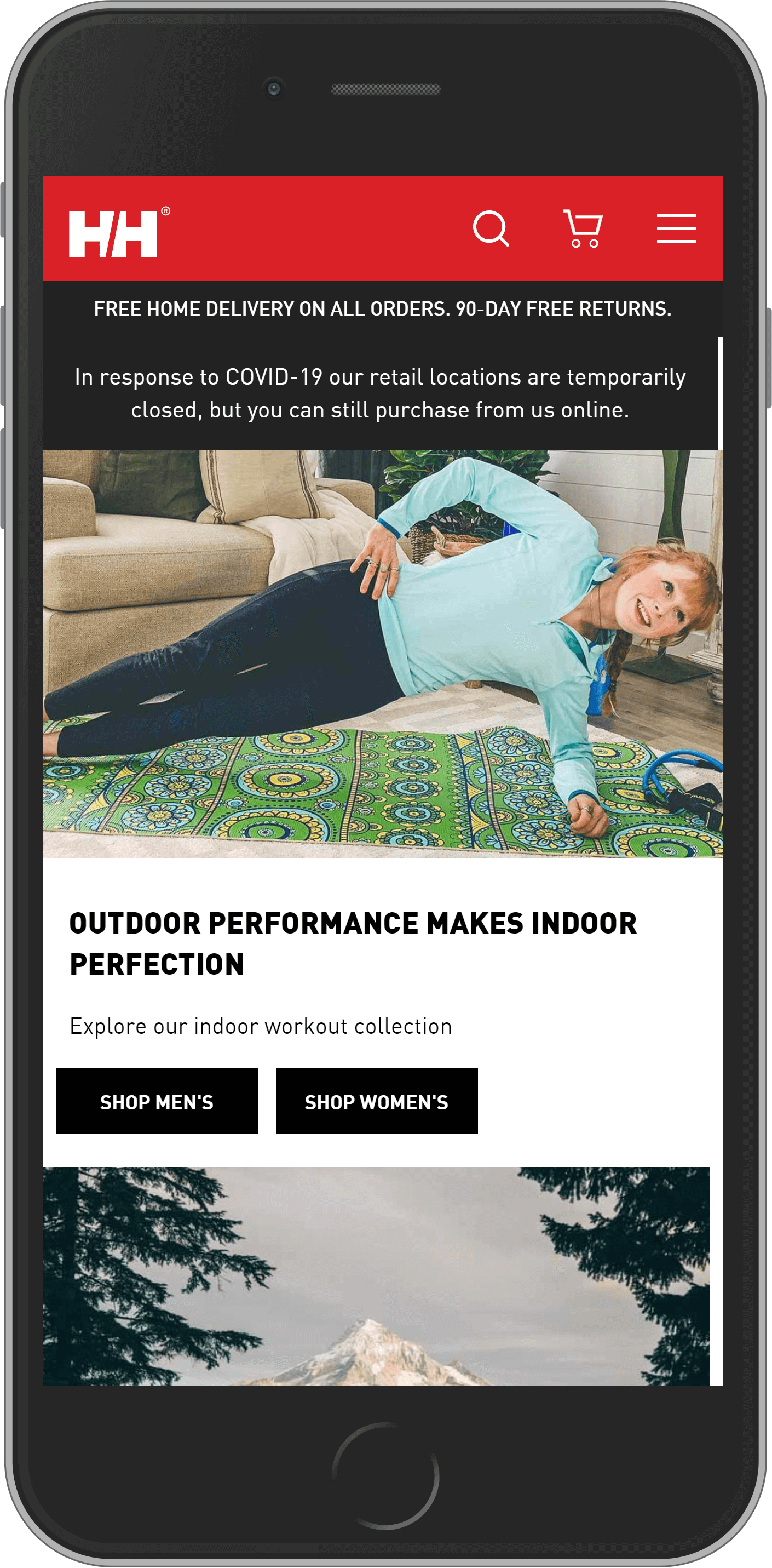
Helly Hansen
Popular Norwegian brand of sportswear and gear for extreme sports is the first on our list of Magento store examples. It’s a company with a long history and deeply-rooted traditions. People all over the world trust their high-quality products. The company has made a name for itself in the global market. In 2019, Helly Hansen held a total revenue of $650.8 million. They continue to develop online stores and increase profits.
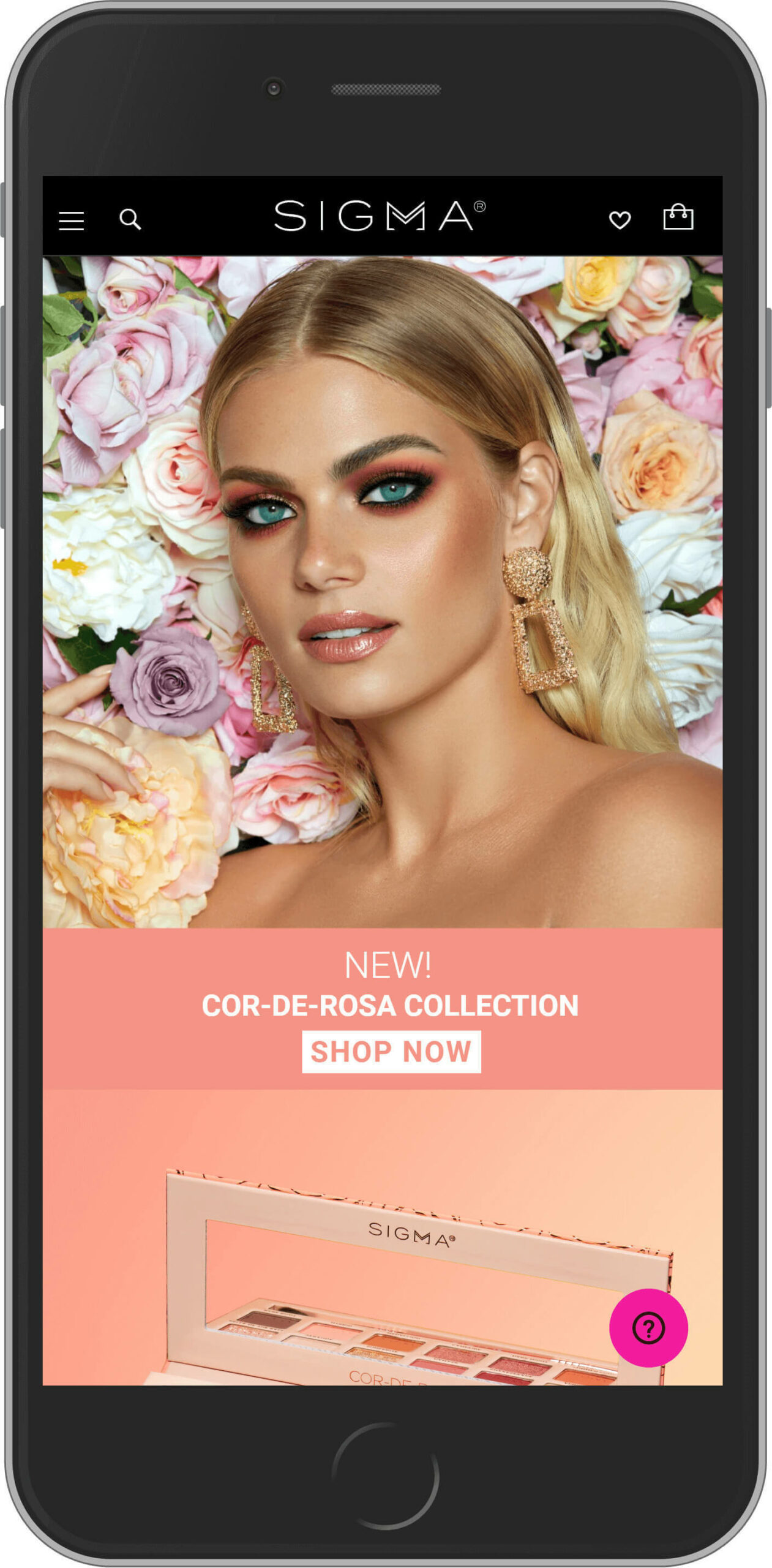
Sigma Beauty
Nowadays, the beauty and cosmetics industry is developing at an incredible pace. Sigma Beauty is a popular British makeup brand. The company was founded in 2009 and reached great success. Their signature makeup brushes have become bestsellers not only in England.
Sigma Beauty leverages Magento 2 and can boast beautiful design and user-friendliness.
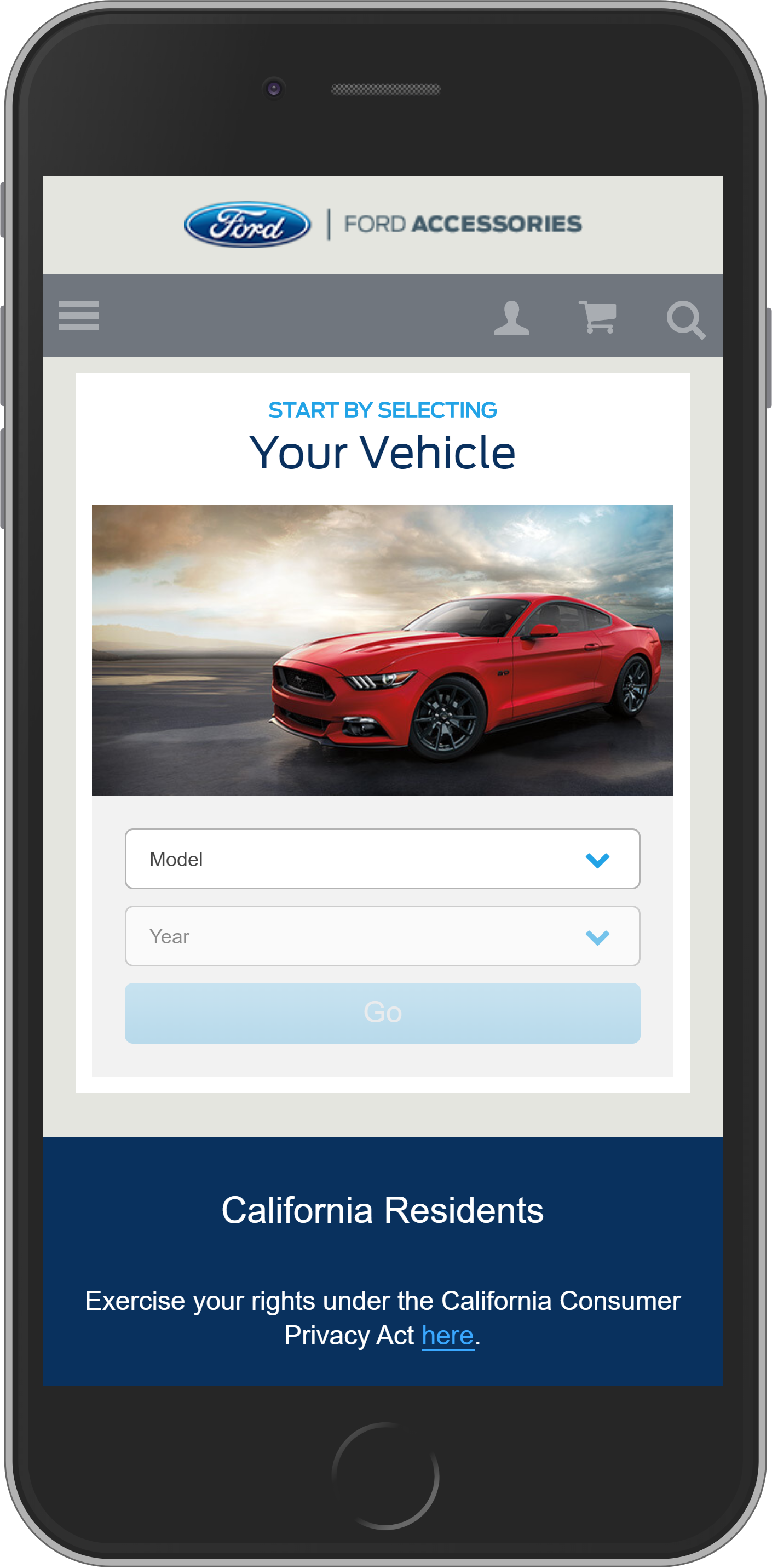
Ford
There’s probably no person in the world who hasn’t heard of this brand. Ford Motor Company is a major player in the automotive industry. Ford is one of the largest car manufacturers, and it ranks 4th place in the world in terms of output over the entire period of existence. One of your friends is most likely to have a car of this brand. And now you know that this American company has the Ford Accessories Online store that has been on our list of Magento website examples since 2012.
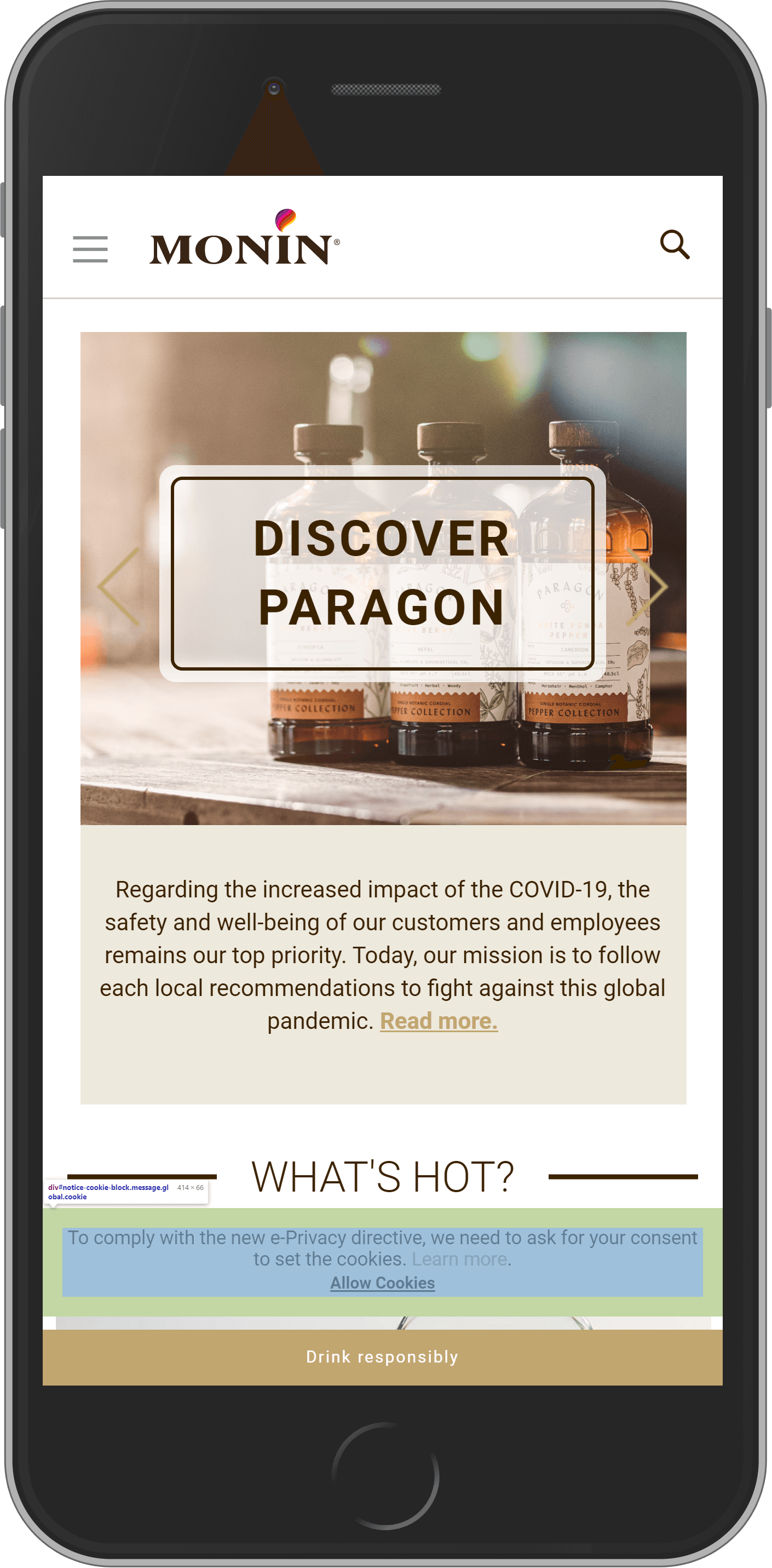
Monin
Monin is another successful member on our top Magento sites list. Who hasn’t tasted their distinguished syrups? It makes us want to drink a cup of caramel coffee or try a cocktail with grenadine. The company is a major player on the international stage of the drinks industry. Monin produces syrups, liqueurs, fruit mixes, frappes, smoothies, and sauces. In 2019, they’ve sold about 100 million bottles.
This online store is delicious. The images of foods create an engaging on-brand experience.
According to the data, available on the official Magento case studies directory, the platform has let Monin increase sales by over 400%, conversion rate―by 20%, and +10% in email-driven revenue. The decision to migrate to Magento 2 has led the company to such impressive results.
“Magento Commerce provided the foundation for development, delivery, and management of a content-rich customer experience to complement a dynamic email strategy proposed by dotmailer.”
Liverpool
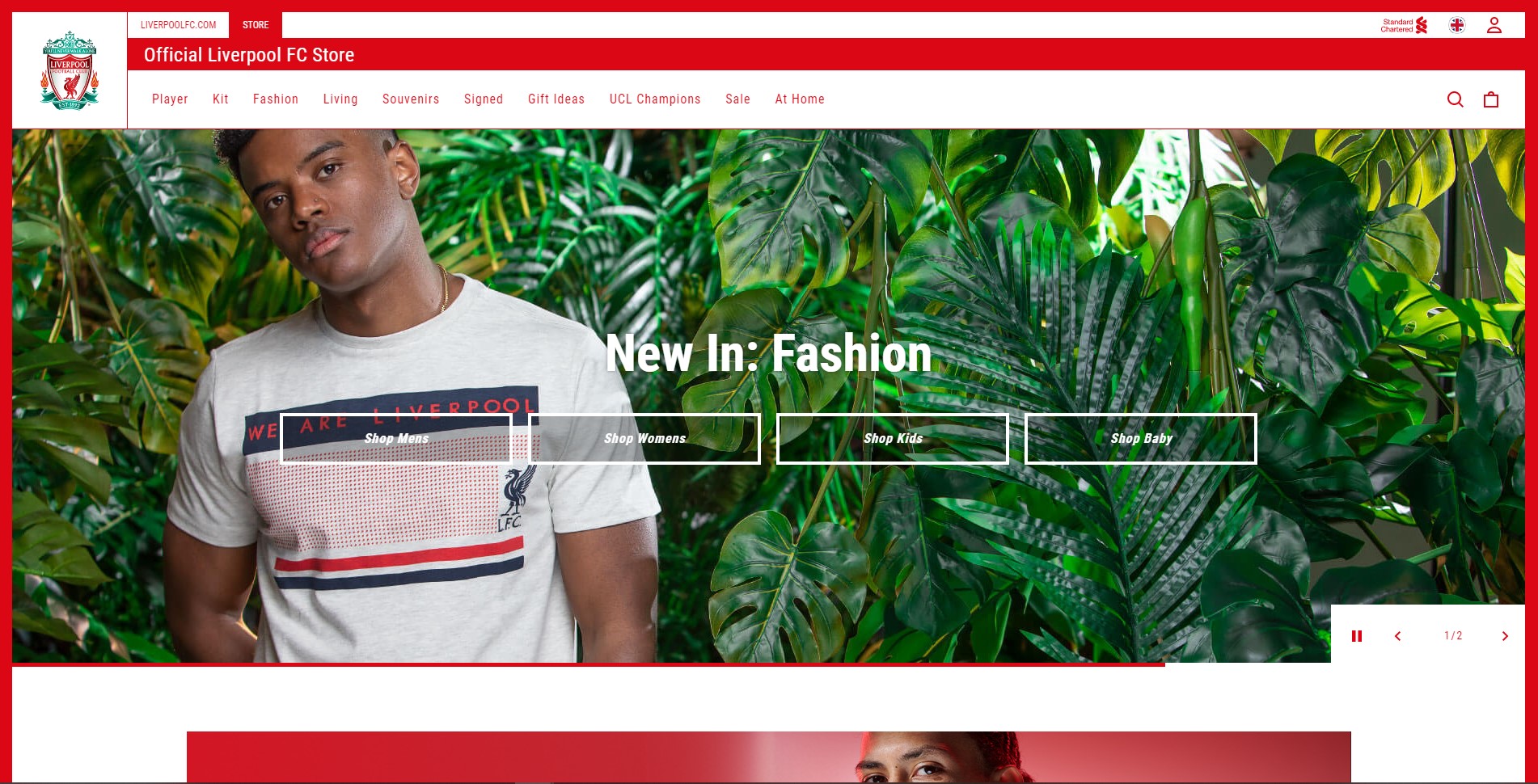
Liverpool FC online store is another business that has opted for Magento 2. A world-famous English football club has its own clothing brand. The online store is very popular with Liverpool fans, which is not surprising. But a great number of people who are not interested in football become regular customers too.

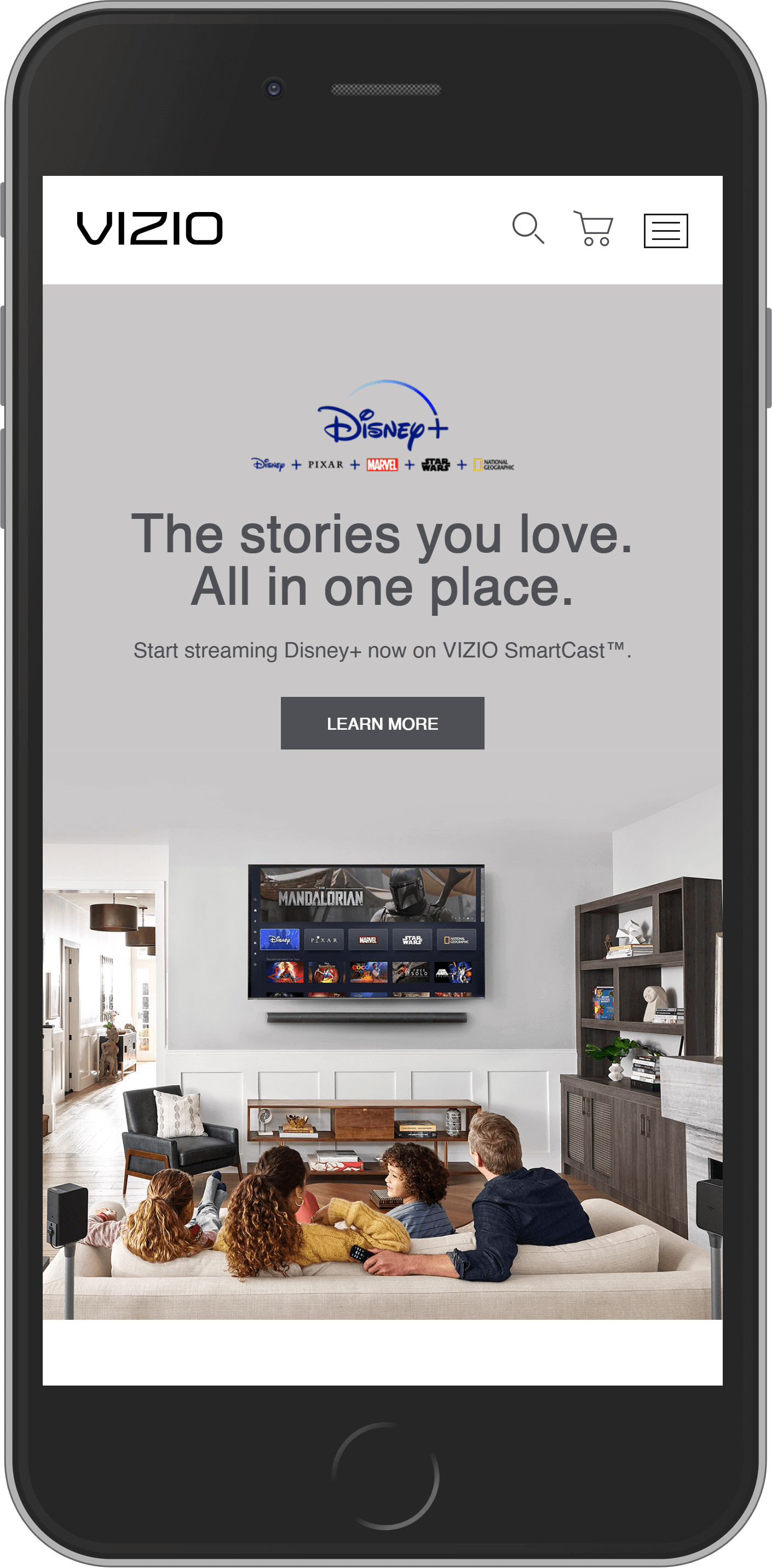
Vizio
Consumer electronics company Vizio is one of the leading manufacturers of TVs and audio equipment. Vizio is a №1 HDTV and Sound Bar brand in the US. It offers products both through retailers and online. Maybe you already have a product of this brand at home.
Being a Magento Enterprise showcase, Vizio is clean and user-friendly. All data blocks are well-structured and welcome visitors on a flawless shopping journey.
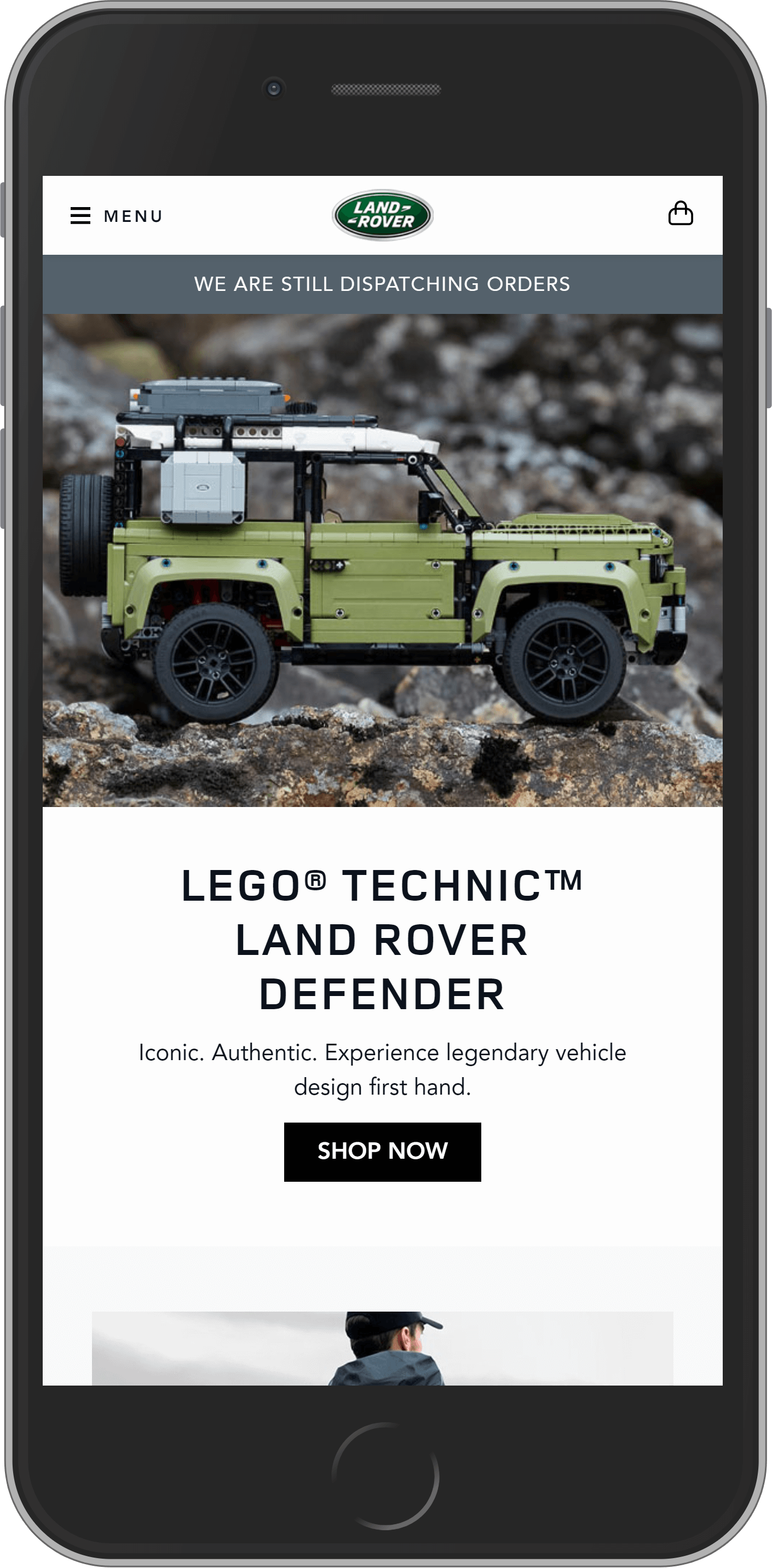
Landrover
Landrover is another splendid car brand on our list powered by Magento 2. Jaguar Land Rover is an incredibly successful British company. Last year they sold more than 480,000 vehicles in 160 countries. More than 80% of the produced cars were exported. And the revenue of the company increased by 8.0% year-on-year to £6.1 billion in 2019.
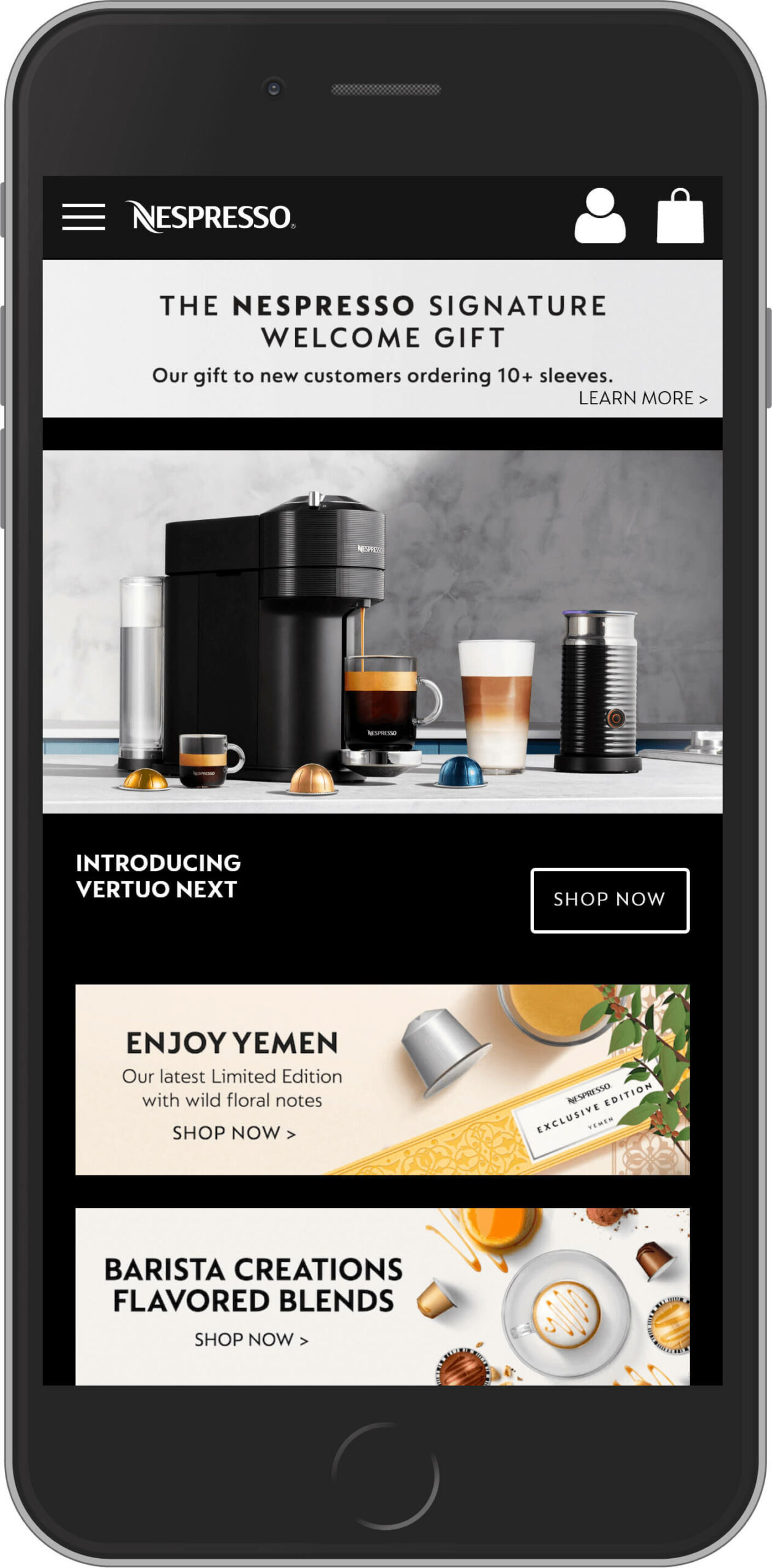
Nestle Nespresso
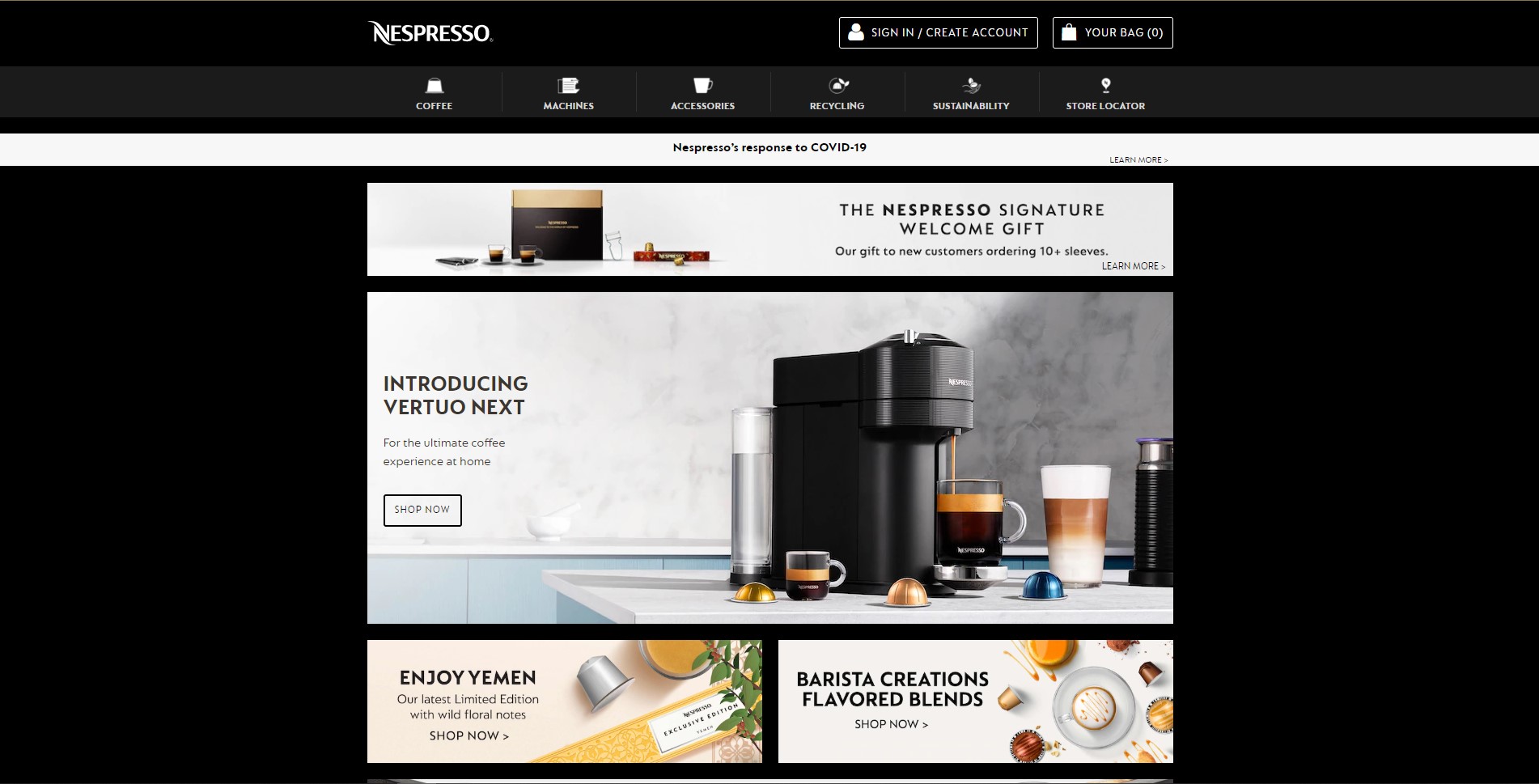
It’s time for a coffee break on our best Magento sites list! Nestle Nespresso is a part of Nestlé Group, the world’s largest food and beverage company. Nespresso offers customers its renowned coffee capsules and high qualitative coffee machines. Nespresso company uses Magento since 2009. Impressive, right?
The mobile version of the site deserves special attention. It’s beautiful, user-friendly, and highly intuitive―all done for an enhanced shopping experience and high conversion rates.
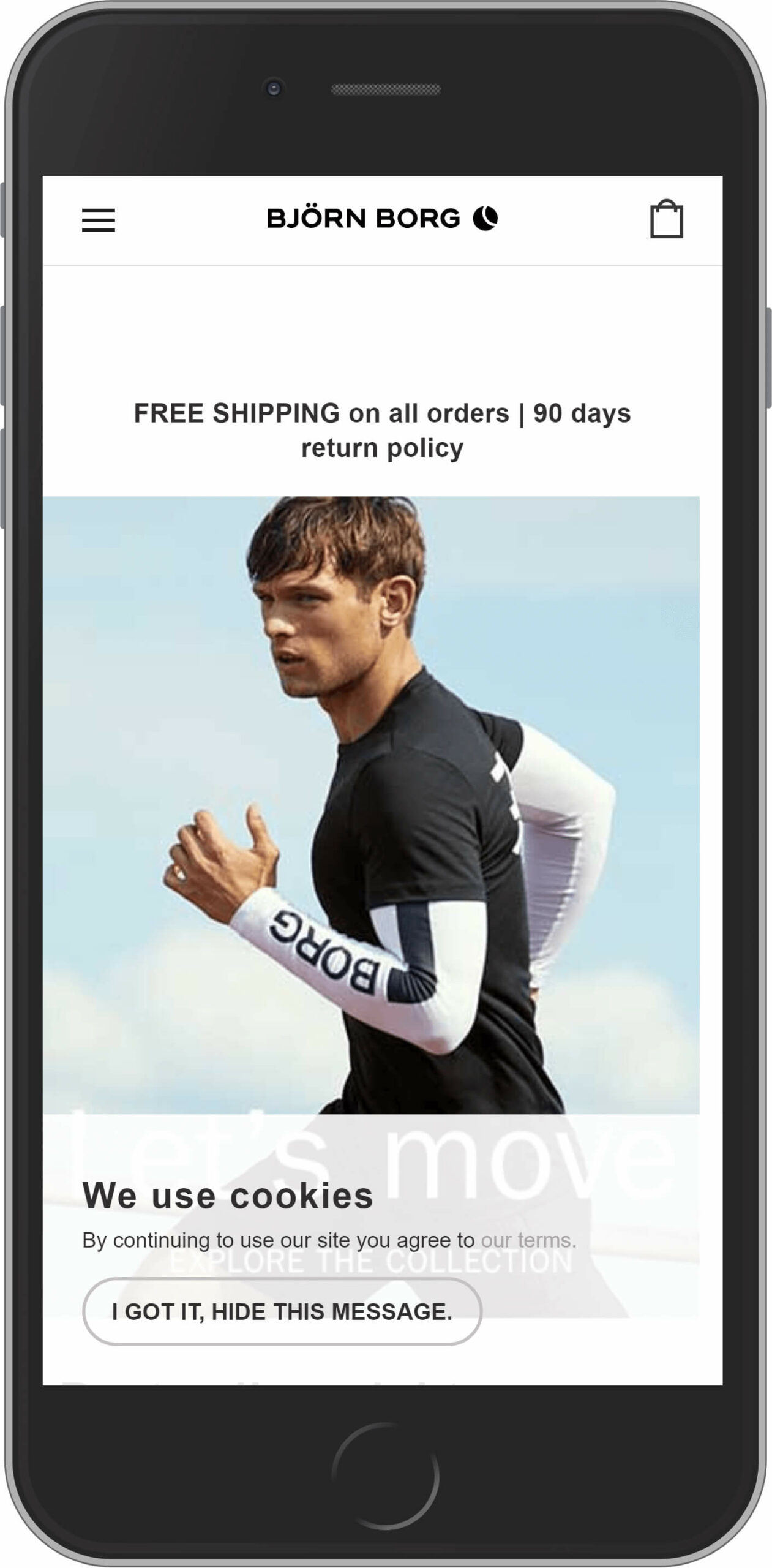
Björn Borg
The company that produces workout underwear is the Magento customer too. This brand was named in honor of one of the greatest players in the history of the sport, Swedish tennis player Björn Borg. Today their products have become popular with sportsmen all over the world.
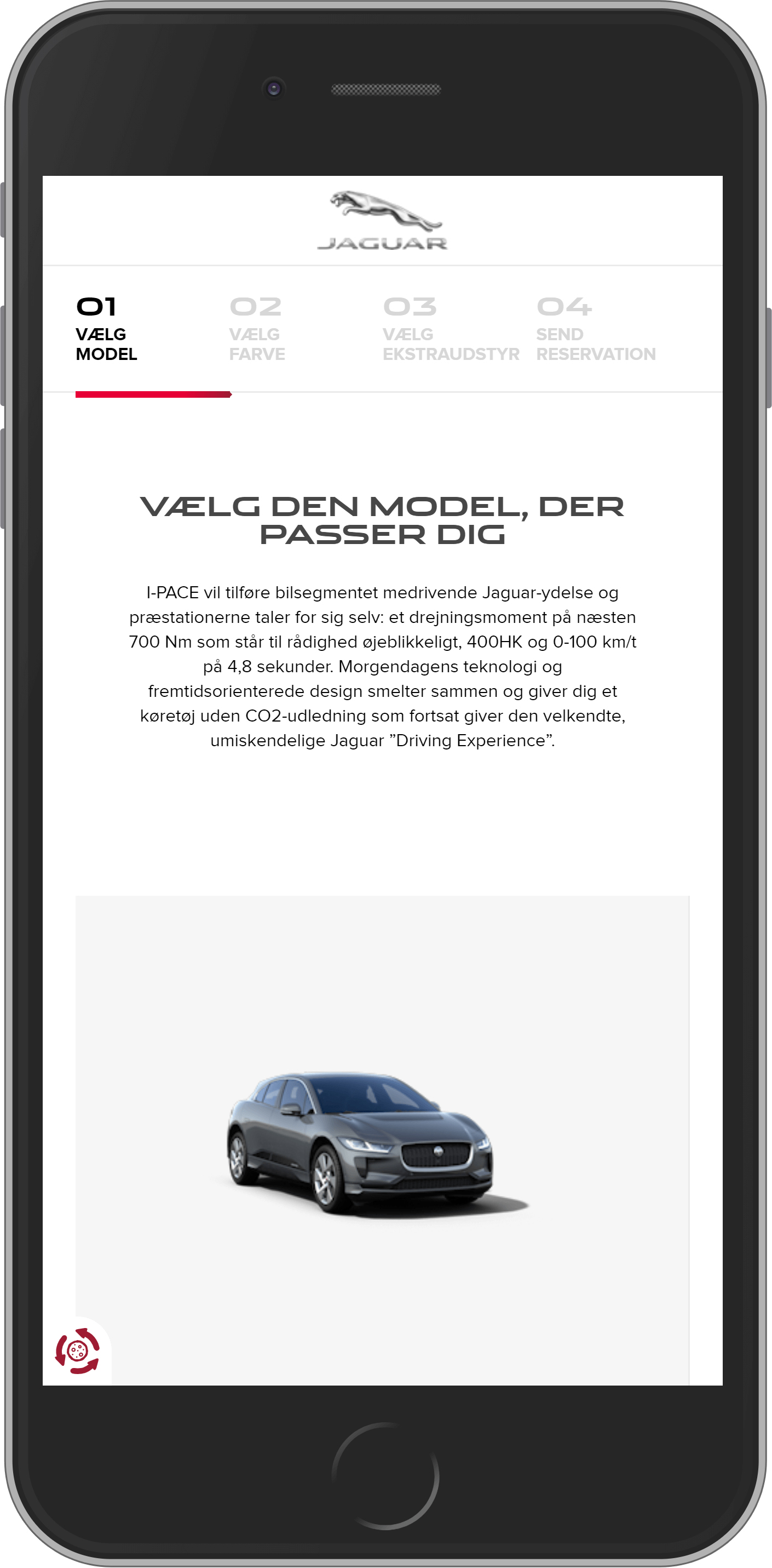
Jaguar
This car brand needs no introduction. Jaguar is well-known for its athletic sports cars and luxurious sedans. A couple of years ago, the company released the electric car model Jaguar I-PACE. In 2016 Nic. Christiansen Group (NCG) become an official retailer of this model in Scandinavia. They launched a Magento 2 website directly for this model. Its appealing design and convenient functionality draws customers and makes it easy to select the model they need.
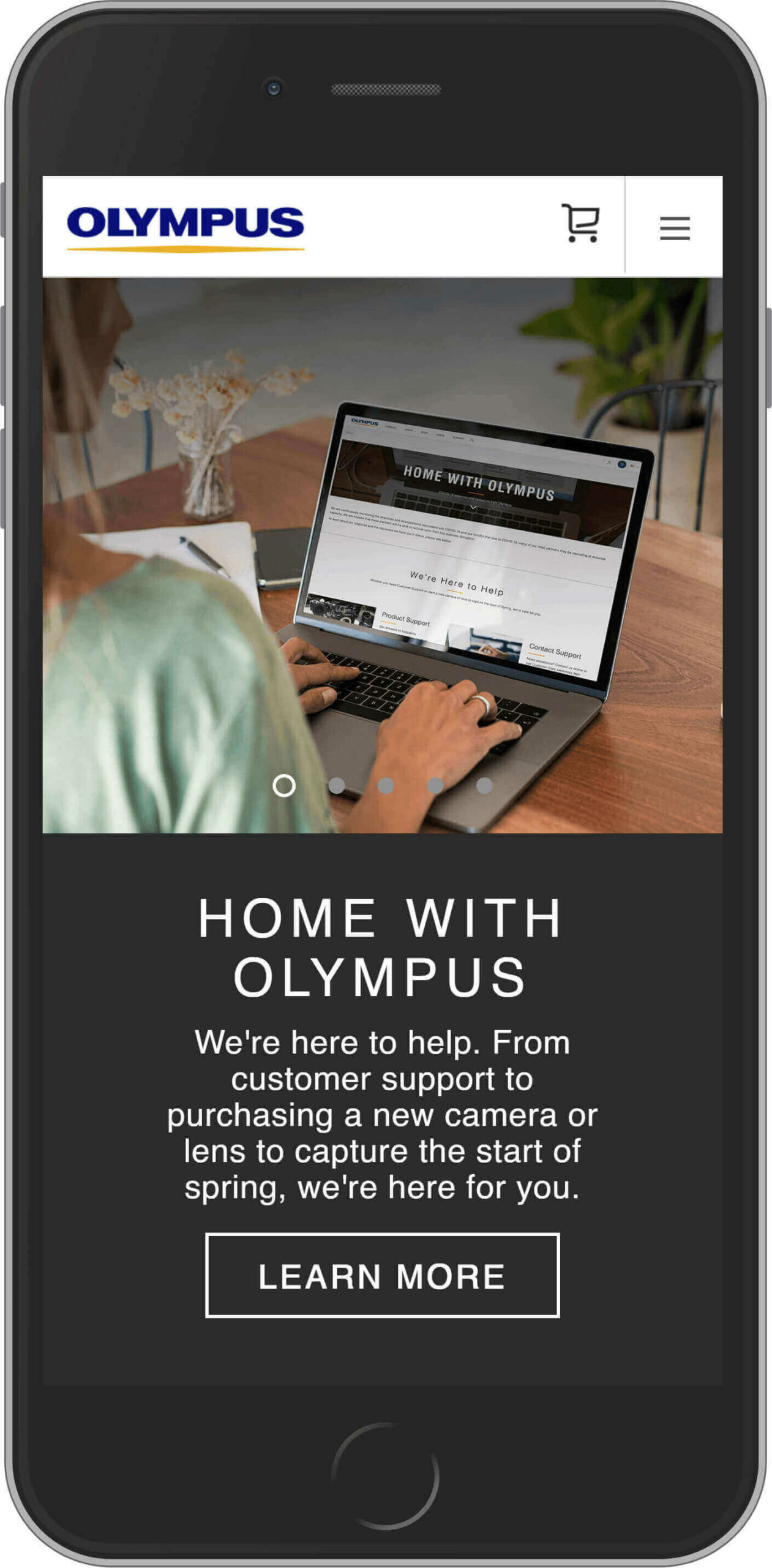
Olympus
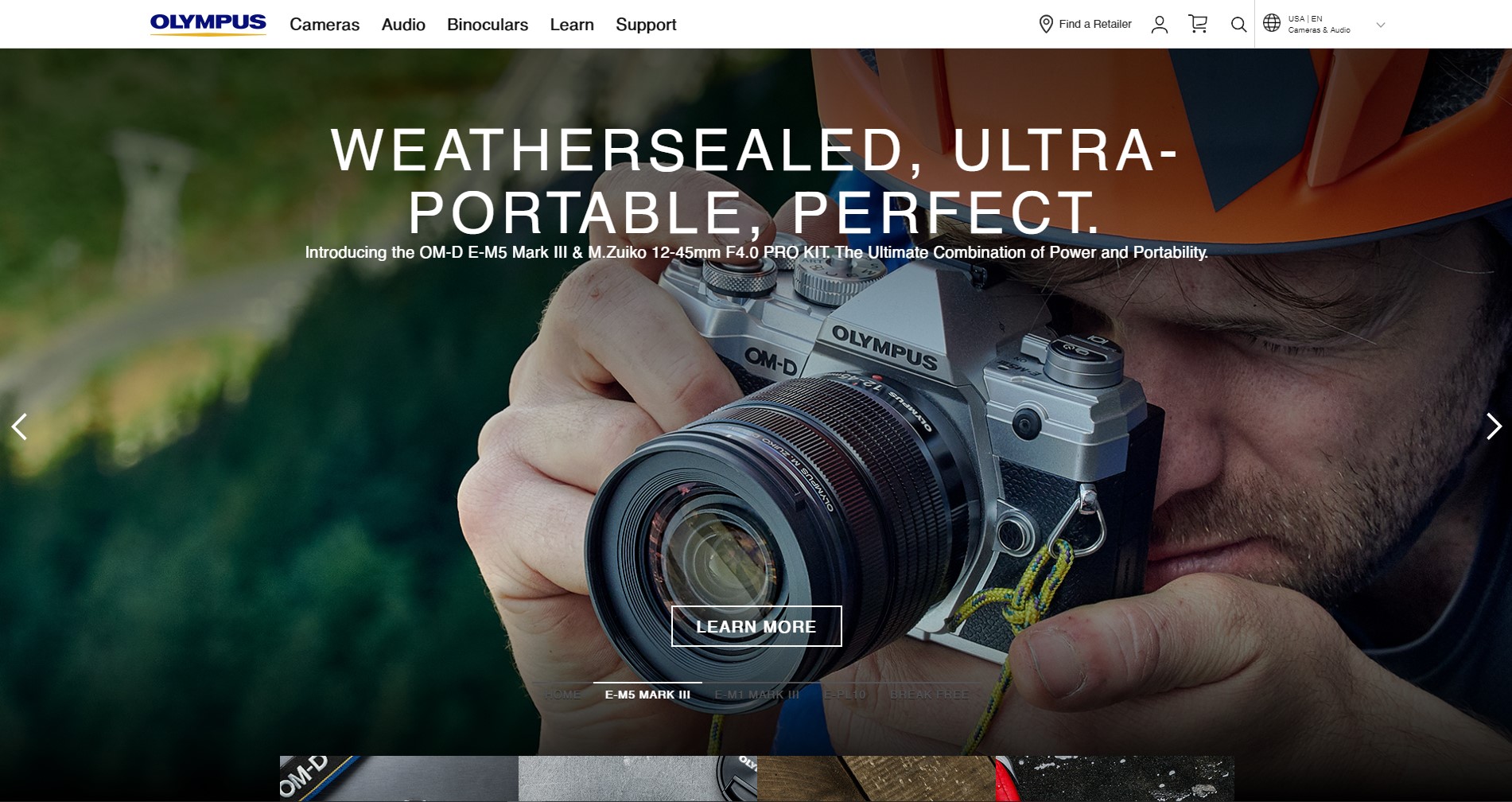
Olympus Corporation is one of the leading manufacturers of optics products and medical and surgical equipment. They are another example of Magento users. Olympus holds roughly a 70% share of the global endoscope market. And probably every photographer is familiar with their cameras. The annual revenue of Olympus for 2019 was $7,145 Billion.
Olympus uses Magento Enterprise as a CMS for its achievements.
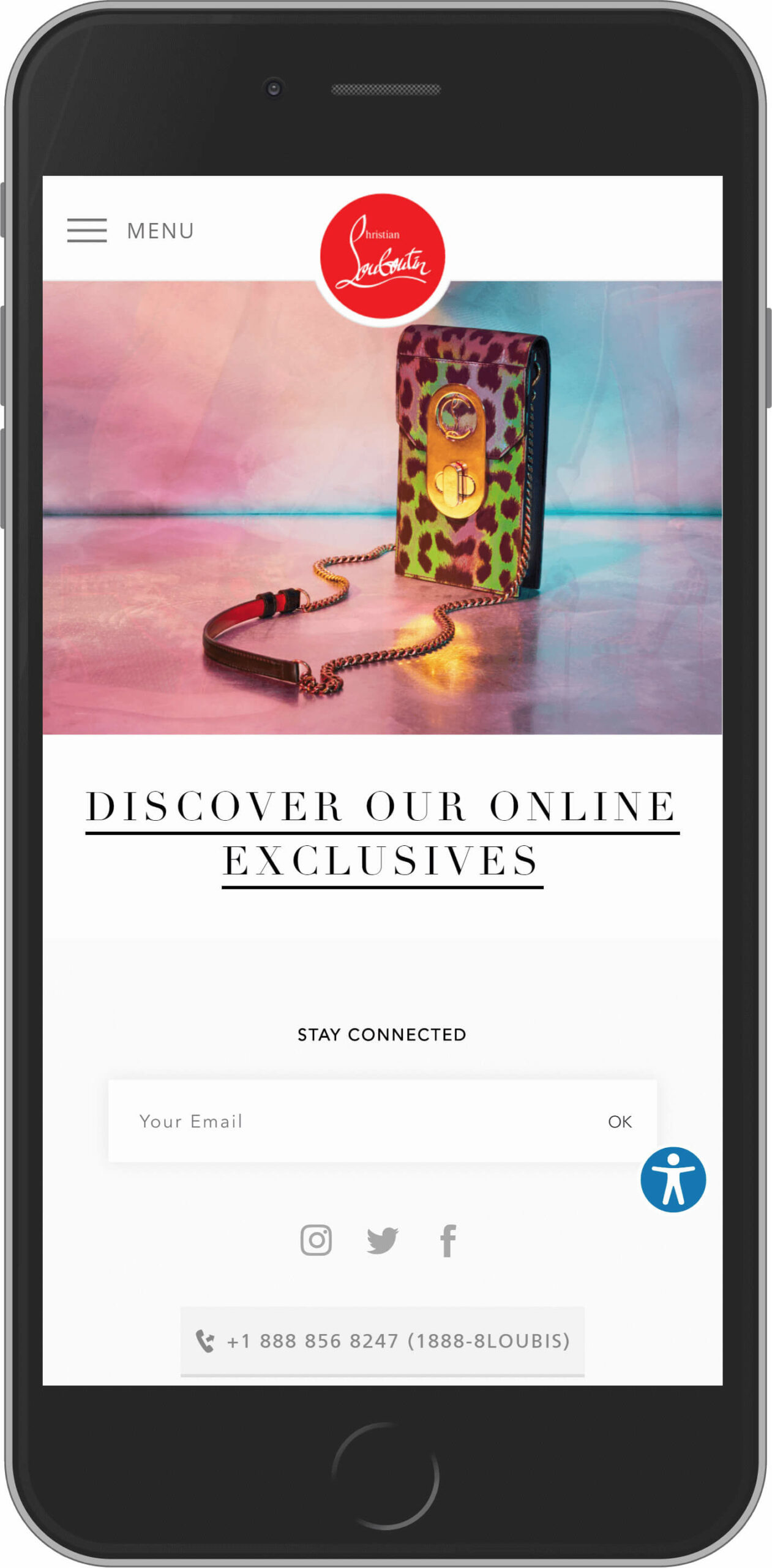
Christian Louboutin
These iconic shoes have made the history of fashion. Every fashionista has at least one pair of Louboutins. This brand has a lot of admirers. Such Hollywood stars as Kim Kardashian, Angelina Jolie, Victoria Beckham, and many others love Christian Louboutin. This French brand also releases bags, accessories, and cosmetics lines.
This Magento site has nothing in access and focuses solely on the product. Its loading speed is worth mentioning as a separate point.
Ahmad Tea

These two words make us recollect the odor of well-known fragrant tea. Ahmad Tea Ltd was founded in 1986 in England. It’s a family business with a rich history. Ahmad Tea has factories in seven countries, including Sri-Lanka and China. You can find their production in 80 countries. The company has a minimalistic, and beautifully designed web store on Magento with a wide range of teas and other products.

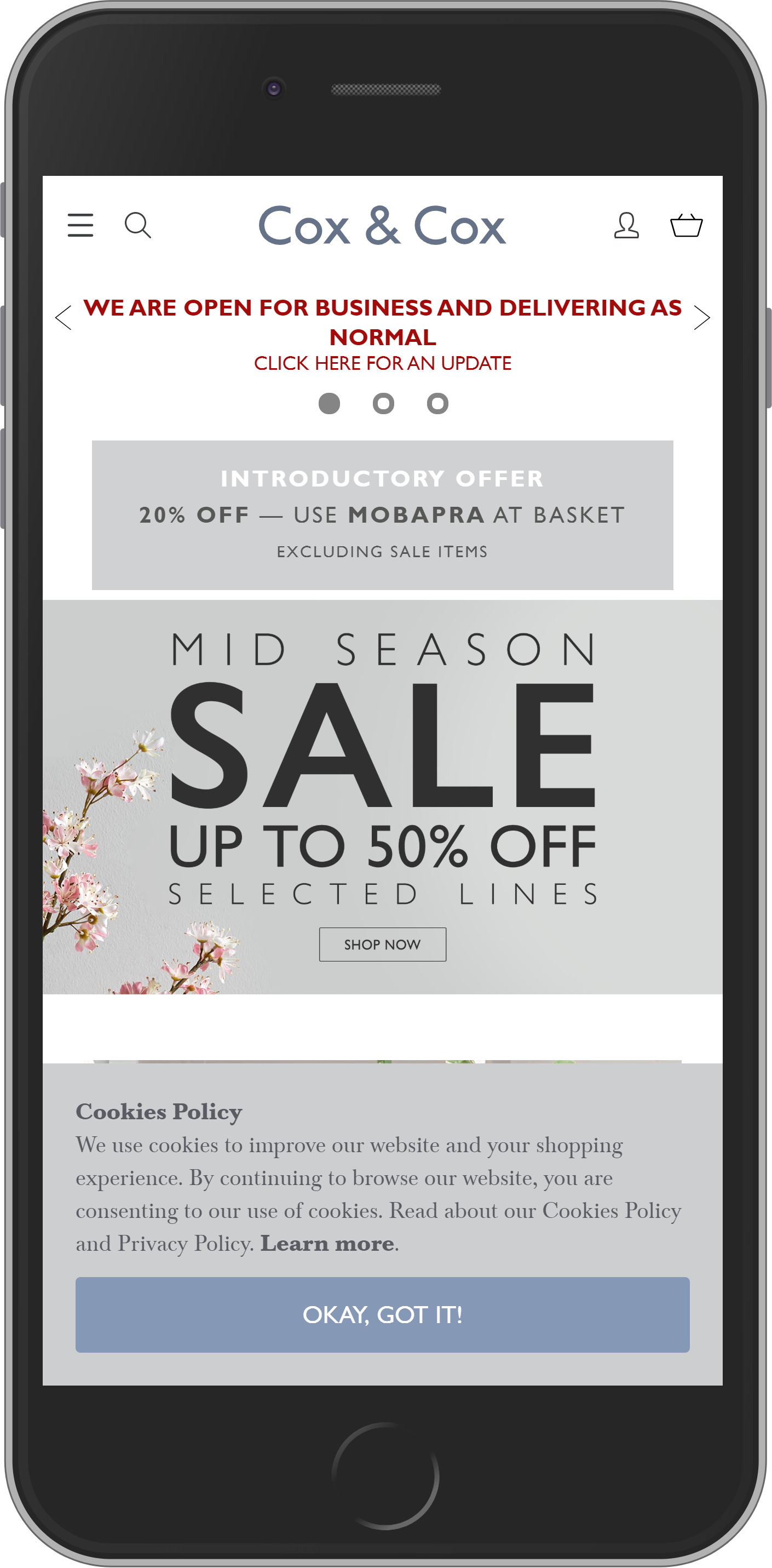
Cox & Cox
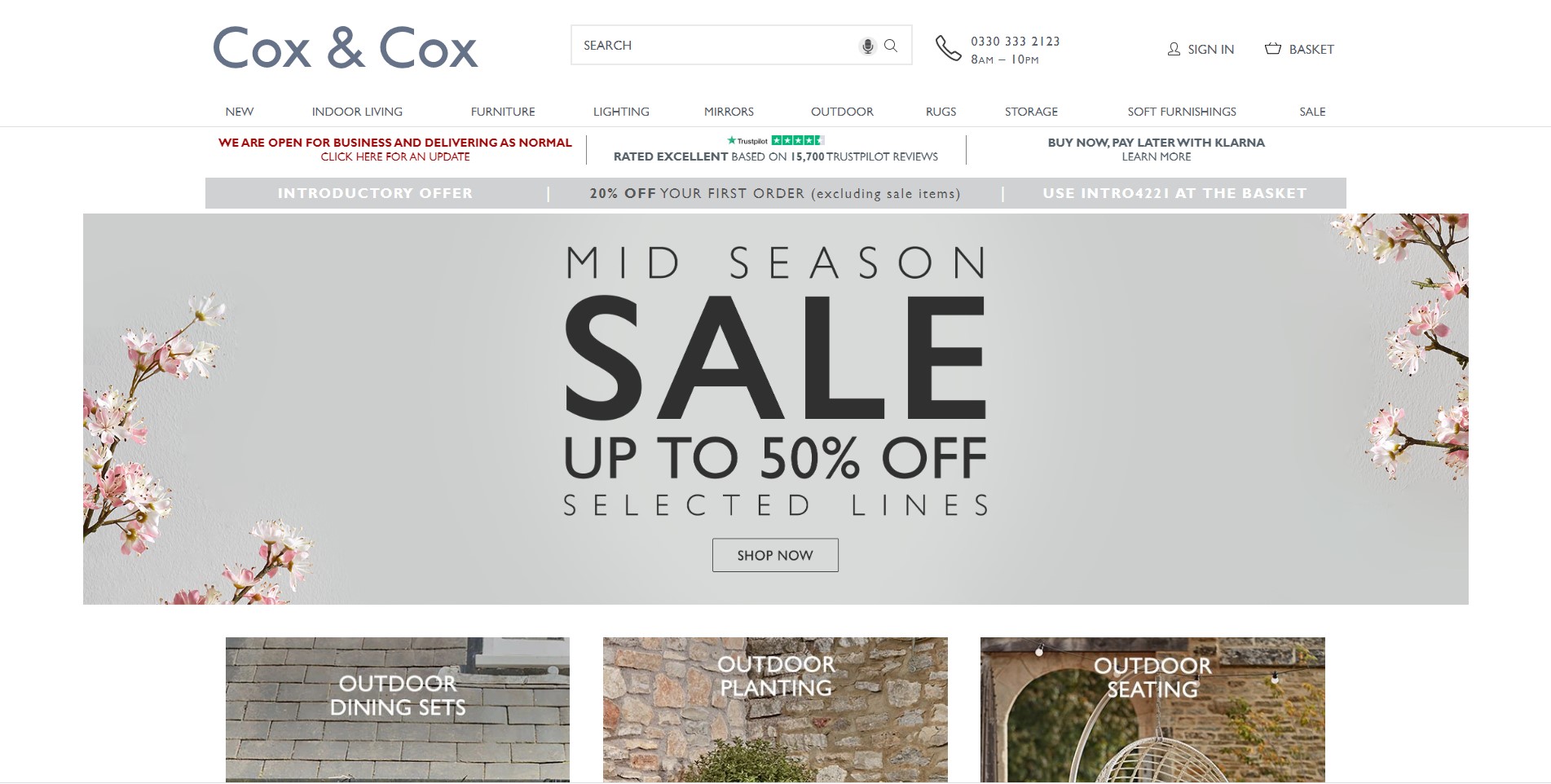
It’s an English brand producing homeware products. If you visit their online store, you’ll find a great variety of distinctive furniture, decorative accessories, and other products. The company always expands its range.
Cox & Cox is one of the sites that use Magento 2, Magento Commerce to be more precise. The site boasts a decent navigation panel with multiple filtering options on the product pages. Additionally, they offer a unique cart to door shipping experience for their customers. All made possible thanks to Magento Shipping capabilities.
Barbour
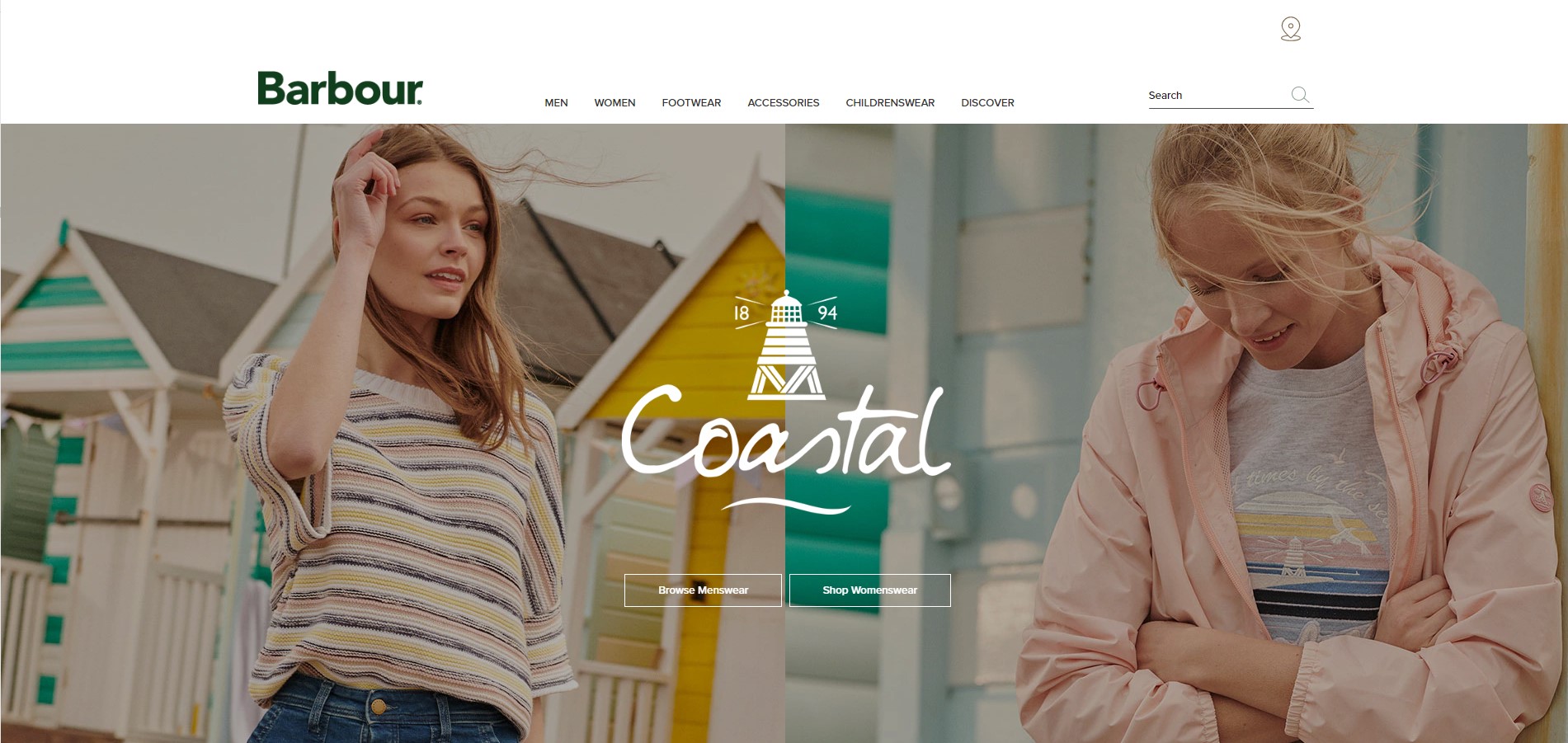
Launched on Magento 2, Barbour is an international fashion brand, which story began back in 1894. It’s a family-owned business, which is run today by the 5th generation! Barbour has its retail stores in 40 countries all over the world and remains true to its core family values.
To Sum Up
As you can see, lots of prosperous world brands give preference to Magento. There are more than 250,000 active web stores using this platform. And it bears fruit! So, maybe Magento can become a good assistant of yours in developing your business too.
We are always there to help you develop a one-of-kind website on the Magento platform or expand the default functionality with the help of our 80+ Magento extensions.
If you think we’ve missed a brand that must be on the top Magento websites list, feel free to leave a recommendation in the comments field.







![[UPDATED] Top 15 Real-Life Examples of Beautiful Magento 2 Websites](https://www.mageworx.com/blog/wp-content/uploads/2016/09/Пост-в-социалки-100x70.jpg)

Your blog is a breath of fresh air in the online world.
I was just looking for this info for a while. After 6 hours of continuous Googleing, finally, I got it in your web site. I wonder what’s the lack of Google strategy that do not rank this type of informative websites in top of the list. Generally, the top websites are full of garbage.